HIPAA vs. SOC 2: Data Security Standards
When it comes to protecting sensitive data, HIPAA and SOC 2 are two key frameworks that serve different purposes but can work together effectively. Here's a quick breakdown:
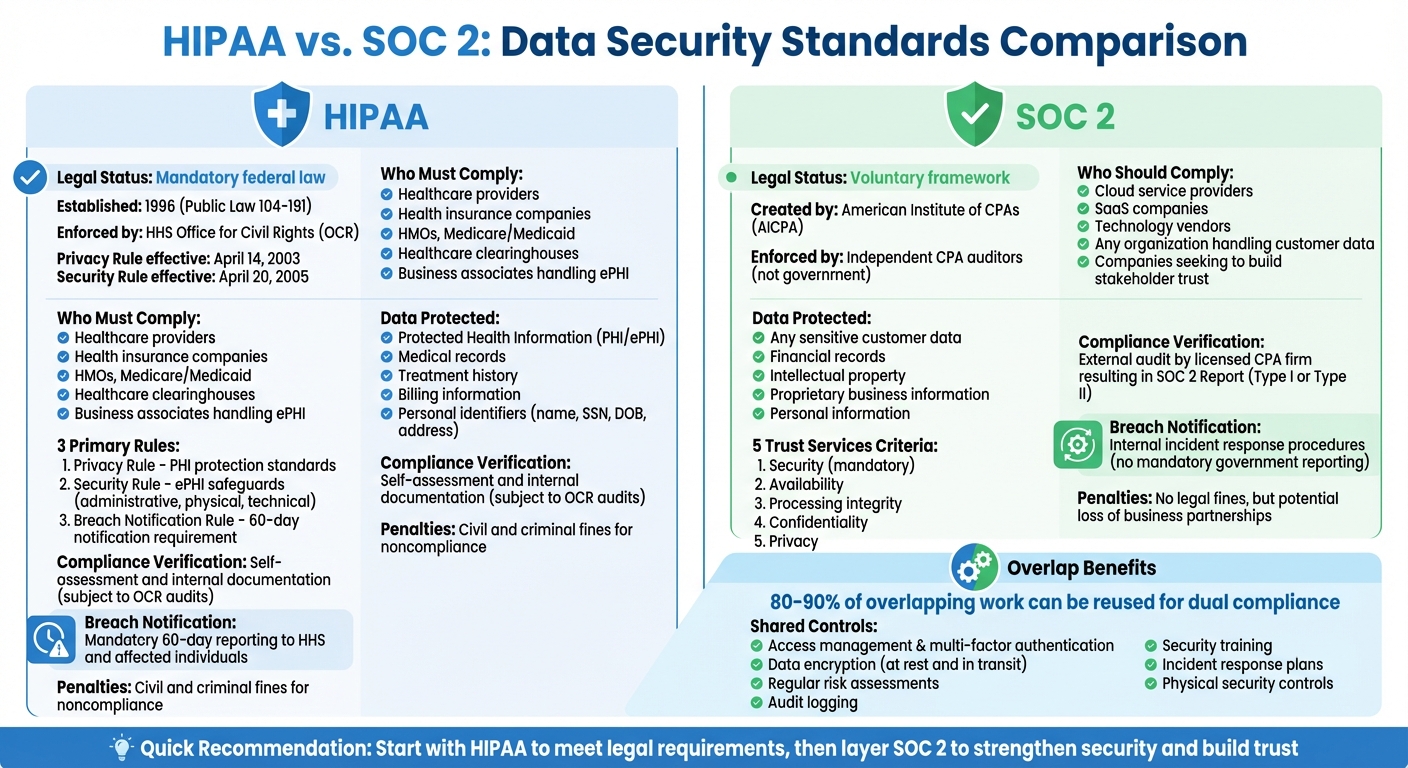
- HIPAA: A federal law that mandates strict safeguards for Protected Health Information (PHI). It's legally required for healthcare providers, insurers, and their partners. Noncompliance can lead to heavy fines or criminal penalties.
- SOC 2: A voluntary framework that audits an organization’s data security practices. It’s widely recognized as proof of strong security, especially for cloud-based systems, but it’s not legally required.
Key Differences:
- HIPAA focuses exclusively on healthcare data (PHI/ePHI).
- SOC 2 covers a broader range of sensitive customer data across industries.
- HIPAA compliance is self-assessed, while SOC 2 requires an external audit.
Why Both Matter:
For recovery centers using advanced CRM systems, HIPAA ensures legal compliance, while SOC 2 builds trust with partners by demonstrating advanced security. Together, they create a comprehensive approach to data protection.
Quick Tip: Start with HIPAA to meet legal requirements, then layer SOC 2 to strengthen your security practices and credibility.
HIPAA vs SOC 2 Compliance Framework Comparison Chart
Legal Requirements and Who Must Comply
HIPAA: Required by Federal Law
HIPAA compliance is mandatory. Established under the Health Insurance Portability and Accountability Act of 1996 (Public Law 104-191) and later reinforced by the HITECH Act of 2009, HIPAA is a federal law overseen by the U.S. Department of Health and Human Services (HHS) Office for Civil Rights (OCR). The Privacy Rule became enforceable on April 14, 2003, while the Security Rule followed on April 20, 2005.
The law applies to covered entities such as health insurance companies, HMOs, Medicare and Medicaid programs, health care clearinghouses, and health care providers (like doctors, dentists, pharmacies, and clinics) that handle certain financial and administrative transactions electronically. Business associates, including billing services, IT vendors, cloud service providers, and their subcontractors who manage electronic protected health information (ePHI), are also directly accountable under the HITECH Act.
"Section 13401 of the HITECH Act... provides that business associates are civilly and criminally liable for penalties for violations of these provisions." - HHS.gov
Noncompliance comes with serious penalties, both civil and criminal, enforced by the OCR. Recovery centers must sign formal Business Associate Agreements (BAAs) with third parties that create, receive, maintain, or transmit ePHI. Additionally, all HIPAA-related documentation must be kept for six years from the date it was created or last in effect, whichever is later.
On the other hand, SOC 2 offers additional security benefits but is not legally required.
SOC 2: Optional but Recommended
Unlike HIPAA, SOC 2 compliance is voluntary. It is not a federal mandate but a framework created by the American Institute of Certified Public Accountants (AICPA) to help organizations demonstrate solid security practices. Compliance is assessed by independent third-party auditors (CPAs), not a government agency.
That said, SOC 2 certification is becoming a standard expectation for many business relationships. For recovery centers, obtaining SOC 2 certification can build trust with stakeholders, enhance reputation, and provide a competitive edge when working with health systems, insurance providers, or state agencies. While failing to meet SOC 2 standards doesn’t result in legal fines, it can lead to lost partnerships and missed business opportunities.
"SOC 2 is not a legal requirement like HIPAA or GDPR, but SOC 2 compliance may be required by prospects, customers, and other stakeholders looking for assurance that you have the systems and controls in place to protect their data." - Secureframe
SOC 2’s framework often aligns with HIPAA’s security requirements, creating overlap that recovery centers can take advantage of. By pursuing SOC 2 compliance, organizations not only bolster their HIPAA efforts but also demonstrate to potential partners that they take data security seriously. Together, these frameworks provide a strong foundation for safeguarding sensitive information.
sbb-itb-ce23a48
Types of Data Each Framework Protects
HIPAA Protects Health Information
HIPAA is all about safeguarding Protected Health Information (PHI). According to the U.S. Department of Health and Human Services, PHI refers to "individually identifiable health information" that is held or shared by a covered entity or its business associate. This can include data in any form - electronic, paper, or even spoken. Essentially, it covers details related to a person’s past, present, or future physical or mental health, the care they receive, or payments for their health care.
PHI often includes personal details like names, addresses, birth dates, and Social Security Numbers. It also covers medical information such as treatment records, medication histories, therapy notes, and billing details. When this information is stored or shared electronically - through emails, cloud storage, or electronic health records - it is classified as Electronic Protected Health Information (ePHI).
However, HIPAA doesn’t cover everything. Employment records and education records governed by FERPA are excluded. Additionally, de-identified data that cannot reasonably be traced back to an individual also falls outside HIPAA’s jurisdiction. Unlike HIPAA, SOC 2 takes a broader approach to data protection.
SOC 2 Covers Multiple Data Types
SOC 2, in contrast, is not limited to health-related information. It focuses on protecting sensitive customer data across various industries, particularly data stored in the cloud. This can include financial records, intellectual property, proprietary business information, and other types of customer data.
The scope of SOC 2 is defined by the Trust Services Criteria, which allow organizations to tailor their compliance efforts. These criteria include Security, Availability, Processing Integrity, Confidentiality, and Privacy. For instance, the "Confidentiality" criterion ensures that sensitive data is protected against unauthorized access using tools like encryption, while "Privacy" governs how personal data is collected, used, and discarded in line with an organization’s privacy policies. This flexibility makes SOC 2 adaptable to the unique needs of different businesses and the specific types of data they handle.
Comparison Table: HIPAA vs. SOC 2 Data Coverage
| Feature | HIPAA | SOC 2 |
|---|---|---|
| Primary Data Protected | Protected Health Information (PHI/ePHI) | Any sensitive customer data (e.g., financial, intellectual property, personal information) |
| Data Format | Electronic, paper, and oral (Privacy Rule); electronic only (Security Rule) | Primarily electronic and cloud-based systems |
| Identifiers Covered | Name, Social Security Number, birth date, and address | Varies based on the selected Trust Services Criteria (Privacy and Confidentiality) |
| Key Exclusions | Employment records and FERPA-governed education records | Depends on which Trust Services Criteria are selected for audit |
| Flexibility | Standardized federal requirements | Customizable based on an organization's operations and selected criteria |
Main Requirements and Compliance Standards
HIPAA's 3 Primary Rules
HIPAA compliance is built around three key rules designed to safeguard patient data. The Privacy Rule (45 CFR Part 160 and Subparts A and E of Part 164) establishes nationwide standards for protecting protected health information (PHI). This applies to information stored on paper, spoken aloud, or saved electronically. The Privacy Rule restricts how covered entities can use or share PHI without explicit patient consent. It also grants individuals the right to access their medical records, request corrections, and see a log of who has accessed their information.
The Security Rule (45 CFR Part 160 and Subparts A and C of Part 164) focuses on protecting electronic PHI (ePHI) by requiring administrative, physical, and technical safeguards. These include conducting risk analyses, training staff, implementing facility access controls, maintaining audit logs, and securing data during transmission.
"The Security Rule requires appropriate administrative, physical and technical safeguards to ensure the confidentiality, integrity, and security of electronic protected health information".
The Breach Notification Rule (45 CFR §§ 164.400-414) requires covered entities to notify affected individuals, the Department of Health and Human Services (HHS), and in some cases, the media, when unsecured PHI is compromised. Notifications must be sent within 60 days of discovering the breach. If the breach impacts more than 500 residents in a specific state or jurisdiction, the entity must also inform prominent media outlets.
While HIPAA provides a federally mandated framework, SOC 2 offers a complementary set of criteria that organizations can tailor to their specific needs.
SOC 2's 5 Trust Services Criteria
Unlike HIPAA's fixed rules, SOC 2 compliance revolves around five Trust Services Criteria, giving organizations flexibility to address various security challenges: Security, Availability, Processing Integrity, Confidentiality, and Privacy. Among these, the Security criterion is mandatory for all SOC 2 audits and serves as the foundation. It ensures systems are secure and reliable.
Availability focuses on keeping systems operational and accessible, emphasizing uptime, network monitoring, and disaster recovery. Processing Integrity ensures that data processing is accurate, complete, and authorized. Confidentiality protects sensitive information through measures like encryption and access controls, while Privacy governs how personal data is collected, used, stored, and shared in line with the organization’s privacy policies.
SOC 2 allows organizations to choose which criteria to include in their audits based on their specific operations and the types of data they manage. This flexibility stands in contrast to HIPAA’s standardized federal requirements, enabling companies to design compliance strategies that align with their unique business needs.
Comparison Table: HIPAA vs. SOC 2 Requirements
| Feature | HIPAA | SOC 2 |
|---|---|---|
| Structural Framework | 3 Primary Rules (Privacy, Security, Breach Notification) | 5 Trust Services Criteria (Security, Availability, Processing Integrity, Confidentiality, Privacy) |
| Mandatory Requirements | All three rules must be followed | Only Security criterion is mandatory; others are optional |
| Security Approach | Administrative, Physical, and Technical safeguards | Common Criteria focusing on access control and system reliability |
| Availability Standard | ePHI accessible on demand by authorized persons | System uptime, performance, and disaster recovery |
| Integrity Definition | Prevention of unauthorized alteration or destruction | Accuracy, completeness, and authorization of processing |
| Implementation Flexibility | "Required" specifications (must implement) vs. "Addressable" (can use alternatives if documented) | Customizable based on selected criteria and business operations |
| Compliance Verification | Internal assessments and documentation (subject to OCR audits) | External audit by licensed CPA firm resulting in SOC 2 Report |
These distinctions highlight the importance of choosing the right compliance framework based on an organization’s operational priorities and the nature of the data it handles.
How Organizations Prove Compliance
HIPAA: Internal Assessments and Documentation
For HIPAA compliance, organizations rely on self-assessments. Recovery centers must conduct internal audits and maintain detailed records of their security practices. There isn’t an official government certification for HIPAA; instead, compliance is demonstrated through documentation and readiness for potential audits by the Office for Civil Rights (OCR).
The first step is a thorough risk analysis to identify potential threats to electronic protected health information (ePHI). Organizations are required to document administrative, physical, and technical safeguards, appoint a security official to oversee policy development, and periodically evaluate their safeguards to ensure they remain effective.
"Conducting a risk analysis is the first step in identifying and implementing safeguards that comply with and carry out the standards and implementation specifications in the Security Rule." – HHS Office for Civil Rights
Recovery centers must also differentiate between "required" specifications, which must be implemented, and "addressable" specifications, where alternative measures can be used if properly documented. Under the 2021 HITECH Amendment, the OCR considers whether an organization has followed "recognized security practices" for the previous 12 months when determining penalties or conducting enforcement actions.
Unlike SOC 2, HIPAA compliance does not involve external audits.
SOC 2: External Audits and Reports
SOC 2 compliance, on the other hand, requires an external audit conducted by an independent, licensed CPA firm. This process results in an official SOC Attestation Report, setting it apart from HIPAA’s self-assessment approach.
The audit begins by defining the scope, including which Trust Services Criteria will be evaluated. Security is mandatory, while other criteria - Availability, Processing Integrity, Confidentiality, and Privacy - are optional. Organizations then align their internal controls with the selected criteria and perform a readiness assessment to identify and address any gaps before the formal audit. Most recovery centers opt for Type II reports, which evaluate controls over a period of 3 to 12 months.
To streamline compliance efforts, Recovery Center CRM centralizes documentation and automates evidence collection. This approach supports both HIPAA and SOC 2 compliance, helping organizations meet federal healthcare requirements while addressing the security needs of business partners and state agencies.
Security Controls Required by Both Standards
Security Measures Both Standards Require
HIPAA and SOC 2 both demand stringent measures to safeguard sensitive data. These include access management with multi-factor authentication and role-based permissions, data encryption for information at rest and in transit, regular risk assessments, and audit logging to track system activity.
Administrative safeguards also align between the two. Both require mandatory security training for employees and the establishment of formal incident response plans to address and document breaches. Physical security measures, like restricting unauthorized access to facilities and data centers, are also key components.
"The Security Rule is designed to be flexible, scalable, and technology neutral, enabling a regulated entity to implement policies, procedures, and technologies that are appropriate for the entity's particular size." – HHS.gov
These shared controls create a consistent framework for protecting sensitive data across systems.
Different Approaches to Vendor Management
When it comes to vendor management, the two frameworks take distinct paths. HIPAA requires vendors handling electronic protected health information (ePHI) to sign a Business Associate Agreement (BAA). This legally binding contract ensures that vendors commit to protecting sensitive data. SOC 2, on the other hand, focuses on vendor risk assessments and ongoing performance monitoring. Organizations are expected to review SOC 2 attestation reports, conduct due diligence, and continuously monitor vendor compliance.
For recovery centers, implementing these practices can simplify the process of meeting both HIPAA and SOC 2 standards. Tools like Addiction Recovery Center and Treatment Center Case Management and CRM by Bee Purple can help streamline vendor management and ensure compliance with both frameworks.
Comparison Table: Shared and Different Controls
| Security Control | HIPAA Requirement | SOC 2 Requirement | Overlap Status |
|---|---|---|---|
| Access Control | Unique user IDs and multi-factor authentication | Role-based access and authentication | High Overlap |
| Encryption | Protect ePHI at rest and in transit | Encryption for sensitive data | High Overlap |
| Risk Assessment | Periodic thorough risk analysis | Continuous risk management | High Overlap |
| Vendor Management | BAAs required | Regular vendor assessments | Different Approach |
| Incident Response | Procedures to identify and respond to incidents | Incident management and resolution protocols | High Overlap |
| Physical Security | Facility access and workstation use controls | Physical access controls to data centers | High Overlap |
| Training | Security awareness and training programs | Regular employee awareness training | High Overlap |
SOC 2 vs HIPAA Compliance: What’s the Difference?
Data Breach Notification Requirements
When it comes to safeguarding sensitive information, recovery centers must understand how to navigate different breach notification protocols to ensure their security measures align with compliance standards.
HIPAA's Mandatory Breach Reporting
HIPAA enforces strict timelines for reporting breaches involving protected health information (PHI). Recovery centers must notify affected individuals and the HHS Secretary within 60 calendar days of discovering a breach. Importantly, the clock starts ticking as soon as any employee becomes aware of the breach.
"A breach shall be treated as discovered by a covered entity as of the first day on which such breach is known to the covered entity, or, by exercising reasonable diligence would have been known to the covered entity." - HHS Regulations
For smaller breaches - those affecting fewer than 500 individuals - there’s a bit more leeway. These can be reported to HHS on an annual basis, but the deadline for submission is no later than 60 days after the end of the calendar year.
Interestingly, if the breached PHI was encrypted and rendered unreadable using HHS-approved methods, notification requirements may not apply. However, in cases where the breach occurs at a vendor, commonly referred to as a Business Associate, the vendor has 60 days to inform the recovery center. Despite this, the recovery center ultimately bears the responsibility for notifying affected individuals.
While HIPAA imposes clear deadlines, SOC 2 takes a different approach, focusing on internal processes rather than statutory notification requirements.
SOC 2's Incident Response Guidelines
SOC 2 shifts the focus from external reporting to strengthening internal incident response. Unlike HIPAA, SOC 2 doesn’t require organizations to notify government agencies about breaches.
Organizations seeking SOC 2 certification must establish and follow well-defined procedures for identifying, responding to, and documenting security incidents. During a SOC 2 Type II audit, which evaluates controls over a 6- to 12-month period, auditors assess whether the organization adhered to its own incident response policies. Recovery centers have the flexibility to set their own timelines based on internal policies or service agreements with clients.
SOC 2 prioritizes operational effectiveness over public disclosure. Instead of mandatory notifications, incidents are reported internally or to affected clients as specified in contractual agreements. The emphasis is on demonstrating sound security practices rather than meeting external reporting deadlines.
Using Both Standards Together in Recovery Centers
Recovery centers need to comply with mandatory HIPAA regulations while also implementing strong SOC 2 practices. This dual approach not only ensures legal compliance but also satisfies the expectations of technology vendors, health plans, and state agencies. By doing so, recovery centers can turn compliance into a powerful tool for enhancing security and operational efficiency, with SOC 2 certification playing a key role.
How SOC 2 Builds Trust with Partners
HIPAA compliance ensures that patient health information is protected as required by law. But SOC 2 goes a step further by providing independent verification, which builds trust with partners:
"Complying with HIPAA demonstrates that your company meets legal requirements, and SOC2 attestation reassures your clients and builds trust in your relationship." - Boston Technology Corporation
For recovery centers, requesting SOC 2 reports from vendors like cloud storage providers or case management platforms is a smart move. These reports verify that the vendors meet strict security standards. For example, a SOC 2 Type II report offers concrete proof that an organization consistently follows its security policies. Platforms such as Recovery Center CRM, which manage documentation across courts, treatment centers, and recovery housing networks, benefit greatly from maintaining both HIPAA and SOC 2 compliance. This dual focus ensures that sensitive data is securely shared between agencies, with strict role-based permissions in place.
Benefits for Recovery Centers
Recovery centers can save time and money by integrating HIPAA and SOC 2 audits. In fact, 80–90% of overlapping work can be reused, allowing for dual compliance reports to be generated from a single audit. This streamlined approach simplifies the process and reduces costs.
The advantages go beyond cost savings. Combining HIPAA and SOC 2 standards helps recovery centers create a secure environment for managing long-term recovery journeys. This is especially important when coordinating transitions from institutional care to community-based support. With robust technical safeguards in place, sensitive documentation stays protected across multiple touchpoints. Automated workflows and effective breach detection ensure data integrity, allowing clinical teams to focus on patient care instead of being bogged down by administrative tasks. By aligning HIPAA and SOC 2, recovery centers not only meet legal and technical requirements but also build stronger partnerships and improve overall operations.
Conclusion: Which Framework Your Organization Needs
After reviewing the essentials of each framework, it’s clear that your organization’s choice should align with its specific needs and legal responsibilities. If your organization deals with Protected Health Information (PHI), HIPAA compliance is a legal requirement. Federal law mandates adherence to strict administrative, physical, and technical safeguards. Failing to comply can lead to steep fines or even criminal penalties.
On the other hand, SOC 2 certification enhances trust with external stakeholders. While it’s not legally mandated, obtaining SOC 2 Type II certification provides third-party validation that your security measures are effective and consistent over time. As Wesley Van Zyl, Head of Customer Success at Scytale, aptly states:
"SOC 2 does not replace HIPAA; it complements it".
This external audit proves especially useful when working with health plans, state agencies, or tech vendors who require evidence of your security practices.
HIPAA and SOC 2 work well together because they share overlapping controls. By aligning efforts in areas like access management, encryption, and breach response, you can comply with both frameworks efficiently, reducing redundant work. This dual approach not only ensures you meet legal and operational standards but also demonstrates a strong commitment to safeguarding sensitive data.
For recovery centers managing complex patient journeys across courts, treatment programs, and community housing, adopting both frameworks creates a robust foundation. HIPAA ensures compliance with legal requirements, while SOC 2 builds trust and highlights operational reliability. Platforms like Recovery Center CRM integrate HIPAA and SOC 2 compliance to facilitate secure data sharing across these intricate networks, using strict role-based permissions.
Start with HIPAA to meet your legal obligations, and then layer SOC 2 to strengthen trust and enhance operational efficiency. This combined strategy transforms compliance from a mere requirement into a competitive advantage, protecting patient information and solidifying your organization’s reputation.
FAQs
Why is it important for recovery centers to comply with both HIPAA and SOC 2 standards?
Meeting both HIPAA and SOC 2 standards is crucial for recovery centers aiming to safeguard sensitive information and uphold trust. HIPAA enforces strict guidelines to protect private health data, ensuring privacy and security. On the other hand, SOC 2 offers a comprehensive framework to secure data integrity, confidentiality, and availability.
By aligning with both standards, recovery centers not only adhere to federal privacy laws but also showcase a strong dedication to operational security. This dual compliance helps shield sensitive recovery-related information, fosters trust among patients and stakeholders, and minimizes the risk of data breaches or regulatory penalties. For centers managing highly personal and critical data, this strategy plays a key role in sustaining long-term credibility and success.
How does SOC 2 certification build trust with partners compared to HIPAA compliance?
SOC 2 certification helps organizations build trust by offering an independent review of their data security practices. Through third-party audits, it evaluates controls related to security, availability, confidentiality, processing integrity, and privacy. The result? Detailed reports that organizations can share with partners, showcasing their commitment to operational reliability and transparency.
On the other hand, HIPAA compliance focuses on meeting federal requirements for protecting protected health information (PHI). However, it doesn’t mandate third-party audits or produce shareable reports. This distinction makes SOC 2 especially valuable for businesses seeking external validation of their security practices, boosting confidence among partners and stakeholders.
How do HIPAA and SOC 2 differ in their approach to data security?
HIPAA and SOC 2 serve different purposes, catering to distinct industries and data protection needs. HIPAA is designed exclusively for the healthcare sector, focusing on safeguarding protected health information (PHI). It enforces strict privacy and security measures to ensure the confidentiality, integrity, and availability of health data. This is achieved through a combination of administrative, physical, and technical safeguards. Compliance with HIPAA is mandatory for covered entities and business associates that handle health-related information.
In contrast, SOC 2 applies to a wider range of industries and is not limited to healthcare. It focuses on managing sensitive data through five trust service criteria: security, availability, processing integrity, confidentiality, and privacy. SOC 2 emphasizes operational controls and cybersecurity practices, offering a more general framework for data protection. While HIPAA zeroes in on health data, SOC 2 takes a broader approach to securing various types of sensitive information.

